How does the encryption keys work?
In this chapter we describe the role of encryption keys in the SALT-solution. The management of keys is an essential part of the solution, as the creation and use of protected templates involve the use of multiple encryption keys that each provide different security and privacy properties.
Three keys
Marked with colours in the figure below, you will find an overview of keys used in the creation of protected templates. There are three encryption keys: “template transformation key”, “homomorphic encryption key” and “sealing key”. The “sealing key” is used to ensure the integrity of the system in the encrypted domain and does not add privacy properties to the protected template.
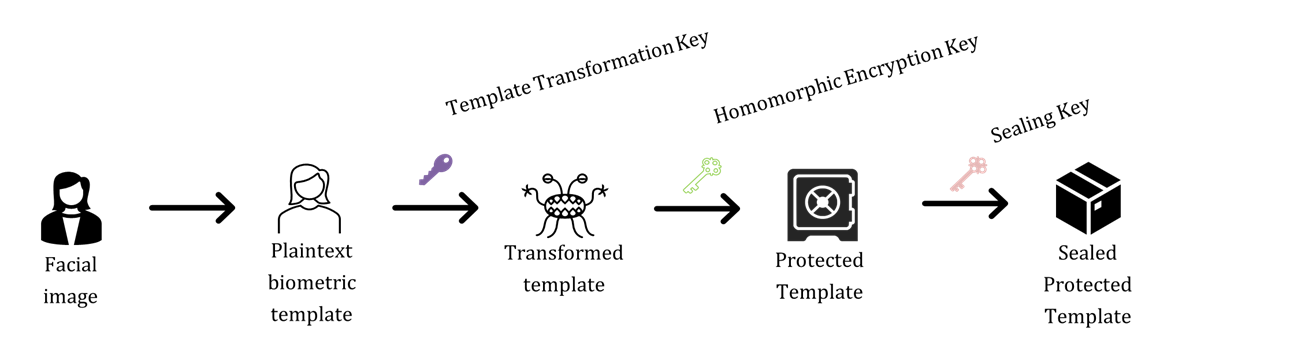
The Template Transformation Key
The first key (“template transformation key”) is used to transform a plaintext biometric template to a transformed template, by combining a “seed” with the transformation process to generate a new and unique version of a plaintext template each time the process is performed. Mobai claims that this transformation provides the privacy properties of irreversibility and unlinkability, in accordance with ISO/IEC 24745:2022.
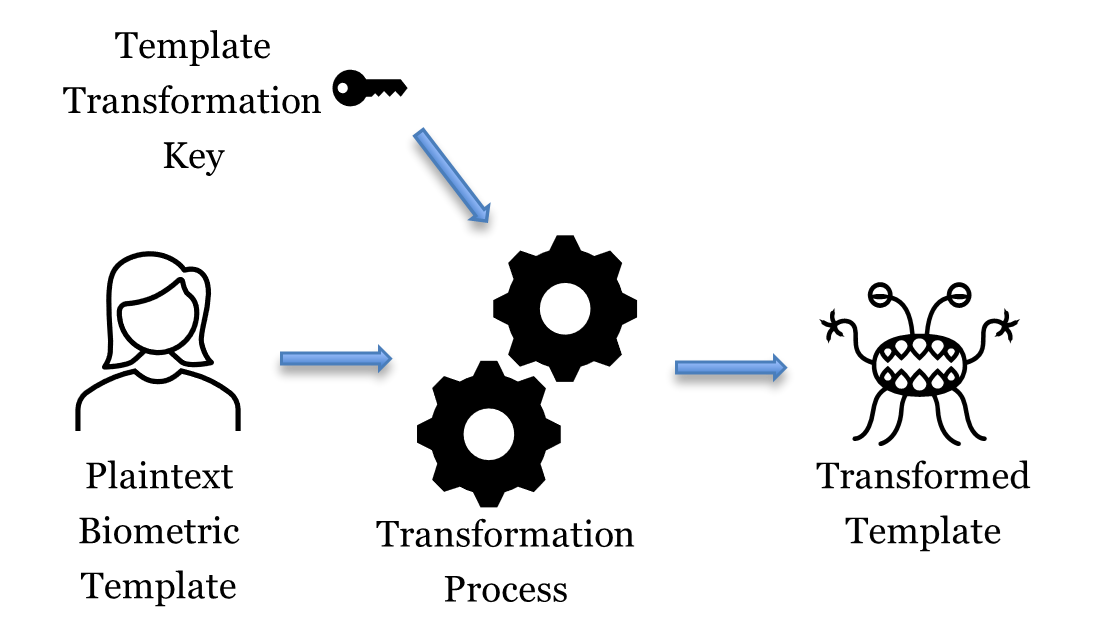
It is assumed to be virtually impossible to re-construct facial features from a transformed template, with the currently known technology, which can ensure the irreversibility of the data. The unlinkability (another requirement according to the ISO) between two protected templates generated from the same person is secured by using different transformation keys for each enrolment.
Furthermore, if a transformed template becomes compromised, the old template transformation key can be thrown away which will render the transformed template unusable, which can claim the revocability of the information. Furthermore, a new transformed template can be created using a new template transformation key, which ensures its renewability.
The transformed template is an intermediate step in the process of generating protected templates. The transformed template is not used for face comparison and is not stored.
The Homomorphic Encryption Key
The second stage is to encrypt the transformed template with a homomorphic encryption key. The output of this encryption is the protected template.
The encryption ensures the confidentiality of the protected template, both at storage and at use. It also ensures confidentiality of the output of the face comparison. This output, which is the similarity score of the face comparison, is the basis for the verification decision. In this system only the output is decrypted.
The homomorphic encryption scheme is based on asynchronous encryption: There are two keys – a key pair – where a data element encrypted by the first key (i.e., the protected template) can only be decrypted by the second key. An important security principle enabled by asynchronous encryption is key separation, i.e., no one entity has access to both keys. In the SALT-solution, the holder of the second key will only have access to the output. This system enables true isolation between the storage and use of the protected templates, and their decryption key. Thus, avoiding single points of compromise in the solution.
The Sealing Key
The sealing key functions as a digital signature and ensures the integrity of the protected template and the output.
This step is using an established scheme for electronic signatures. The verification process should validate this signature before each use of a protected template.
Key Management
Mobai intends to manage the keys in a way that ensures the confidentiality of these processes. The key management system will generate and manage keys in secure environments. The template transformation key is generated using a strong random number generator with sufficient length, and the homomorphic encryption key is generated using the latest homomorphic encryption scheme. A cryptographic key management policy will be implemented by following ISO 27001 standards.